10 Ways to Set Up WordPress .htaccess Security
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

You’ve already heard about hackers targeting vulnerable websites and wondered if yours might be next. You want to lock down your site and keep it safe, but you’re not sure where to start. Thankfully, there’s a powerful tool already at your fingertips—the .htaccess file.
The .htaccess file allows you to set rules that control the flow of traffic to your site. It can perform some of the traffic moderation that a good firewall does, simply by adding a few lines of code.
However, we understand that editing the .htaccess file can feel daunting, especially when you consider the potential risks. Will it affect your live site? Could it cause unexpected downtime? You might be afraid that one wrong step could mess up your whole website.
These are valid concerns, and knowing how to safely add scripts and modify this important file is crucial. The good news is that by being very cautious and following a few essential guidelines, you can enhance your site’s security without unnecessary complications.
TL;DR: Enhance your WordPress site’s security by using the .htaccess file. It can protect vital directories, enforce SSL, and block unauthorized access. For an easier, automated solution, try MalCare’s intelligent firewall and vulnerability protection.
This guide will walk you through everything you need to know to secure your WordPress site using the .htaccess file, step-by-step. You’ll learn which scripts to add and how to do them correctly to ensure your site remains live and functional while you bolster its defenses. By the end, you’ll feel confident in managing your site’s security.
Note: Always take a full backup of your site, including its files and database, before editing a system file like .htaccess. Backups can be lifesaving if you make any mistake in editing the .htaccess file and your site crashes.
1. Protect wp-config.php file
The wp-config.php file is one of the most critical files in your WordPress installation. It contains essential information about your site’s configuration, including database settings, security keys, and various other sensitive details.
Since the wp-config.php file holds such sensitive information, unauthorized access to it can lead to severe security breaches, including database access and potential site takeovers. Thankfully, you can restrict access to wp-config.php using the .htaccess file and ensure that it remains hidden from prying eyes.
To do this, add the following code snippet to your .htaccess file:
<files wp-config.php>
order allow,deny
deny from all
</files>2. Block directory browsing
WordPress is immensely popular, which means many people are familiar with its directory structure. This familiarity can be a double-edged sword, making it easier for hackers and unauthorized visitors to navigate your site’s directories. All they need to do is simply add the directory path to your site URL and they can find sensitive information or vulnerabilities. To keep your website secure, it’s essential to block directory browsing, which prevents people from viewing the contents of your directories.
To do this, add the following code snippet to your .htaccess file:
Options -Indexes3. Block access to wp-content
The wp-content directory is a crucial part of your WordPress site. It contains uploads, plugins, themes, and other important files, including PHP scripts. Unfortunately, this makes it a prime target for hackers looking to exploit your site. Hackers can gain access to this directory and inject malware or upload malicious files. In the worst-case scenario, they can also take control of your site. This can lead to data theft, site defacement, and even server-wide infections. Hence, blocking unauthorized access to the wp-content directory becomes a vital security measure.
But, it’s important to note that blocking access to the wp-content folder can interfere with plugin updates, installs, and other functionalities. Many users put in place this security measure and then unblock access when needed. Now, this approach may add a layer of complexity. But, it enhances your site’s security by preventing unauthorized access.
To do this, add the following code snippet to your .htaccess file:
# Block access to specific wp-content subdirectories
<Directory "wp-content">
Order allow,deny
Deny from all
<Files ~ ".(jpg|jpeg|png|gif|css|js)$">
Order allow,deny
Allow from all
</Files>
</Directory>4. Implement security headers
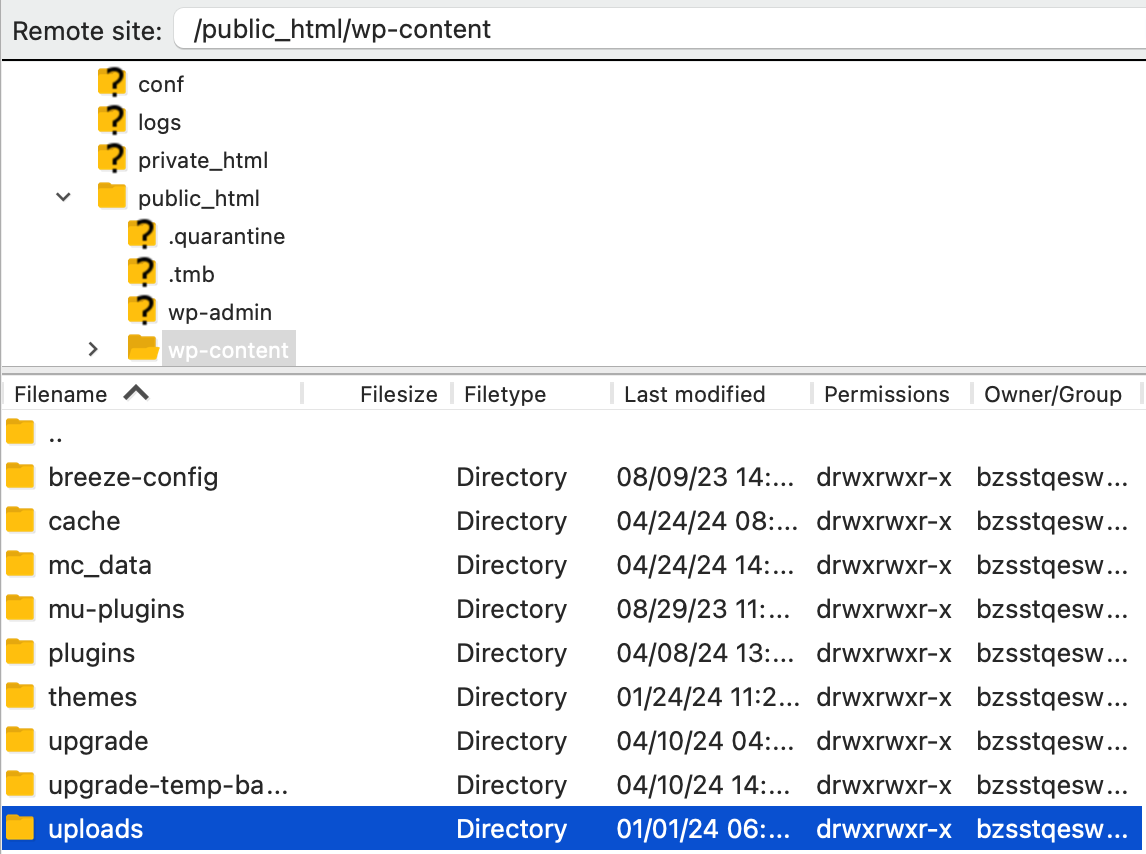
Security headers are crucial for protecting your WordPress site against various types of cyber threats. This includes attacks such as cross-site scripting (XSS), clickjacking, and other code injection attacks. By instructing the browser on how to handle your site’s content, security headers add an extra layer of defense. This ensures that potential vulnerabilities are closed before they can be exploited.
Security headers are customizable and provide rules to the browser about how to treat your website’s data. For instance, security headers can restrict the sources from which your site can load scripts, disallow the embedding of your site in frames, and enforce content security policies.
To implement security headers, you can add the following code snippet to your .htaccess file:
# HTTP Strict Transport Security (HSTS)
Header set Strict-Transport-Security "max-age=31536000" env=HTTPS
# X-Content-Type-Options
Header set X-Content-Type-Options "nosniff"
# X-Frame-Options
Header set X-Frame-Options "SAMEORIGIN"
# X-XSS-Protection
Header set X-XSS-Protection "1; mode=block"
# Content Security Policy
Header set Content-Security-Policy "default-src 'self'; script-src 'self' 'unsafe-inline' https://cdnjs.cloudflare.com; object-src 'none';"This code snippet shows the most commonly set rules for security headers. You can always adjust them as needed for your site.
5. Restrict PHP files and their execution
Restricting PHP execution in specific directories is an effective way to enhance your WordPress site’s security. By disabling PHP execution in directories where its use is unnecessary, you significantly reduce the risk of malicious scripts being executed. This helps protect your site from common attacks such as PHP injections, which can be devastating if hackers manage to upload and run malicious PHP files.
Common directories where PHP execution is often unnecessary include the wp-content/uploads, wp-includes, and other media or asset folders.
To do this, add the following code snippet to a new .htaccess file within each targeted directory:
<Files *.php>
deny from all
</Files>6. Enforce SSL
Enforcing SSL (Secure Sockets Layer) on your WordPress site is essential for ensuring the data transferred between your website and its visitors is protected. SSL enhances your site’s security by encrypting sensitive information, such as login credentials and personal details. This makes it much harder for cybercriminals to intercept and misuse this data.
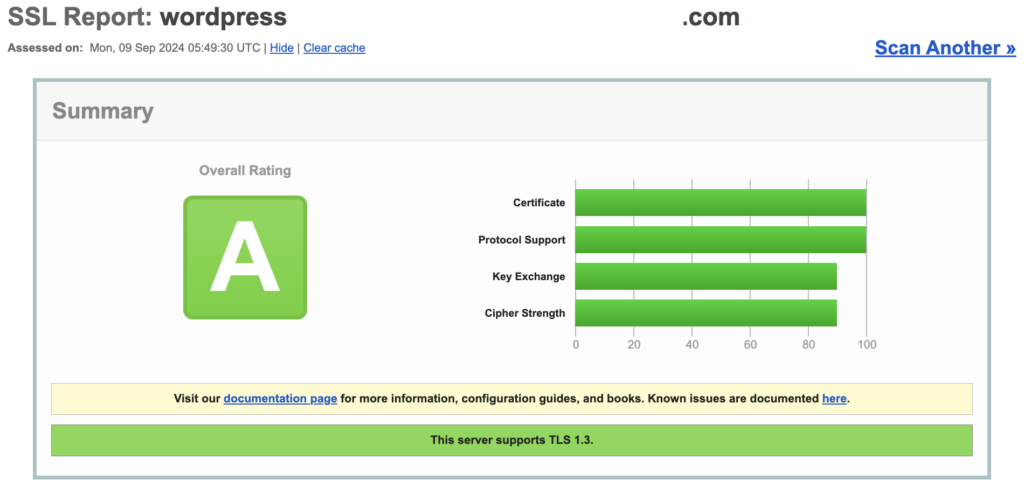
Moreover, SSL certifications boost user trust as visitors can easily recognize your site as secure, thanks to the padlock icon displayed in their browser’s address bar. Additionally, having SSL positively impacts your SEO rankings, as search engines like Google prioritize secure websites in their search results.
Enforcing SSL on your site ensures all visits are directed to the secure HTTPS version of your website.
To do this, add the following code snippet to your .htaccess file:
# Enforce SSL
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
</IfModule>7. Disable access to XML-RPC
The xmlrpc.php file in WordPress enables communication between your site and third-party applications, such as mobile apps and external services. While this functionality can be useful, it also opens up a potential path for hackers to exploit. Cybercriminals often target the xmlrpc.php file to launch brute force attacks, DDoS (Distributed Denial of Service) attacks, and other malicious activities. If you’re not using any third-party applications that require XML-RPC, it’s prudent to disable access to this file to enhance your site’s security.

By disabling access to xmlrpc.php, you effectively close this vulnerability, ensuring that hackers cannot use this entry point to compromise your WordPress site. This straightforward measure significantly reduces the risk of unauthorized access and other malicious activities.
To do this, add the following code snippet to your .htaccess file:
# Disable access to xmlrpc.php
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>8. Block author scans
Hackers often use author scans to gather the usernames of signed-in users or authors on your WordPress site. By knowing valid usernames, they can mount brute-force attacks to guess passwords and gain unauthorized access to your site. Preventing author scans helps protect against these kinds of attacks and adds a layer of security to your WordPress installation.
Blocking author scans is a crucial step in safeguarding user accounts, especially if your site has multiple contributors. This measure thwarts automated scripts and attackers from easily finding usernames, making it significantly harder for them to execute brute-force attacks.
To do this, you can add the following code snippet to your .htaccess file:
# Block author scans
RewriteEngine On
RewriteBase /
RewriteCond %{REQUEST_URI} ^/author/(.*)$
RewriteRule .* - [R=403,L]9. Protect .htaccess from unauthorized access
After setting various security safeguards in your .htaccess file, it is essential to protect the .htaccess file itself from unauthorized access. Ensuring the .htaccess file remains secure is crucial because it contains the rules that help maintain your site’s integrity and security. If malicious actors can access and modify this file, they can potentially undo all your security measures and gain control over your site.
To protect the .htaccess file from unauthorized access, you can add a specific rule within the file itself. This rule will prevent any external access to the .htaccess file, ensuring that only you (and your server) can read or modify its contents.
To do this, add the following code snippet to your .htaccess file:
# Protect .htaccess file
<Files .htaccess>
Order allow,deny
Deny from all
</Files>10. Blacklist suspicious IPs and enforce geoblocking
Blocking suspicious IP addresses and enforcing geoblocking can enhance your WordPress site’s security by preventing access from malicious sources. This can be particularly useful if you notice unusual traffic patterns, such as high request rates from specific IPs at odd times, or repeated attempts to access your site from locations you don’t serve.
However, it’s essential to note that maintaining a blacklist of IP addresses can be cumbersome and may not be practical in the long term, as new malicious IPs appear constantly. Instead of manually managing IP blacklists, consider using MalCare’s Atomic Security firewall for automated, comprehensive protection against malicious traffic.
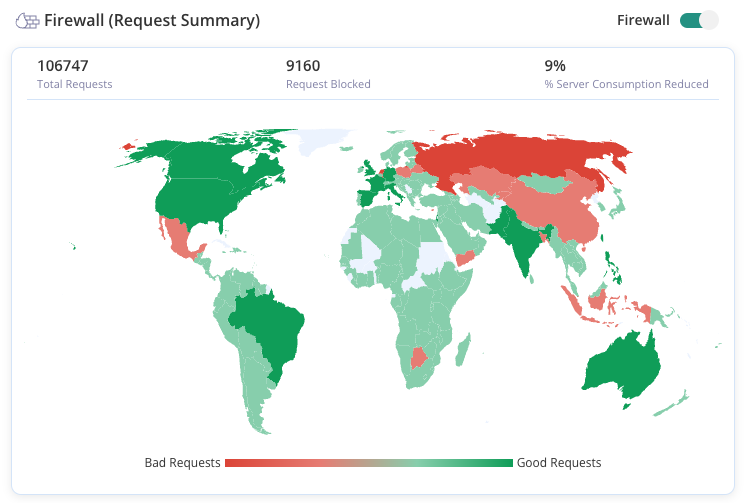
To do this, you can add the following code snippet to your .htaccess file:
# Block specific IP addresses
<Limit GET POST>
Order Allow,Deny
Allow from all
Deny from x.x.x.xReplace x.x.x.x with the suspicious IP addresses and repeat the Deny from directive for every new IP address
How to edit the .htaccess file
Editing the .htaccess file is crucial for implementing various security measures and configurations on your WordPress site. It’s vital to know the different methods available to edit the .htaccess file safely. Our comprehensive guide can help you with detailed steps to do this.
Note: Always take a full backup of your site before editing a system file like .htaccess. This way, you can easily restore your site if something goes wrong.
Troubleshooting
Editing the .htaccess file can significantly enhance your WordPress site’s security and functionality, but it also carries the risk of causing errors or unintended consequences. This section will help you troubleshoot common issues that may arise after modifying the .htaccess file and provide tips on how to mitigate potential problems.
1. 500 Internal Server Error: This is usually caused by syntax errors in the .htaccess file. Recheck all the code you added to the .htaccess file to ensure there are no typos or misplaced characters. If the error persists, try commenting out recent changes (#) to identify the problematic line.
2. Blocked your own access: Sometimes you might end up accidentally blacklisting your own IP address. In such scenarios, use FTP or cPanel to access and edit the .htaccess file. Remove the line that blocks your IP. Consider switching to a different internet connection or using a VPN to change your IP address temporarily if you’re completely locked out.
3. Googlebot blocked: If you have inadvertently blocked Googlebot or other search engine crawlers, it may result in search engines not displaying your site or its content in search results. Ensure that your .htaccess rules do not block legitimate search engine bots. You can use the Allow from directive to explicitly permit access for Googlebot.
# Allow Googlebot
<IfModule mod_setenvif.c>
SetEnvIfNoCase User-Agent "^Googlebot" allow_googlebot
</IfModule>
<FilesMatch ".*">
Order Deny,Allow
Deny from all
Allow from env=allow_googlebot
</FilesMatch>4. Mixed content warnings: Enforcing SSL is necessary to ensure secure connections to your site. However, this may result in some resources not loading over HTTPS after enforcing SSL. Ensure all internal links, scripts, and media files are updated to use HTTPS. You can use the Really Simple SSL plugin to set resources to load over HTTPS.
If you cannot resolve an issue, you can reset the .htaccess file to its default state for WordPress. Here’s the default content for a typical WordPress installation:
# Default WordPress .htaccess file
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPressThis is why we recommend you always backup your site before making any changes to system files and avoid any issues.
Easy alternative to great security: MalCare
Blocking access to hackers is what .htaccess security is all about, but there are easier and more efficient ways to achieve the same goal. A robust firewall can filter malicious IPs, customize geoblocking, and disable PHP execution without you ever needing to touch the .htaccess file.
MalCare’s Atomic Security offers comprehensive, automated protection, leveraging an intelligent firewall to keep your site safe. It efficiently handles tasks like disabling XML-RPC, limiting file access, and preventing brute-force attacks, providing continuous security through an intuitive, user-friendly dashboard.
Using MalCare simplifies the process while ensuring robust, ongoing protection against cyber threats. For hassle-free, effective security, consider MalCare’s advanced solutions and keep your WordPress site secure without the complexities of manual .htaccess edits.
Final thoughts
The .htaccess file can be an effective way to secure your WordPress site. You can add rules to reduce vulnerabilities and counter various cyber threats. This includes brute force attacks, unauthorized access, and other malicious activities. Just remember to back up your .htaccess file before you make any changes.
While editing the .htaccess file offers granular control, it can be time-consuming and complex. This is where a robust security plugin like MalCare comes into play. MalCare provides comprehensive security features like an advanced firewall, bot protection, and vulnerability detection. It can ensure superior protection for your site without the need to edit the .htaccess file.
FAQs
What is a .htaccess file?
The .htaccess file is a configuration file used by Apache web servers to manage server settings. It can control a wide range of server behaviors, including URL redirection, access restrictions, security settings, and more. For WordPress sites, it plays a critical role in managing permalinks and enhancing site security.
How do I edit the .htaccess file safely?
Always backup your .htaccess file before making any changes. You can edit it using FTP, cPanel’s File Manager, or a WordPress plugin like WP File Manager. Follow best practices to avoid syntax errors, and test your site after making changes to ensure everything works correctly.
What should I do if I encounter a 500 Internal Server Error after editing .htaccess?
A 500 Internal Server Error usually indicates a syntax problem in your .htaccess file. Recheck the code you added and ensure there are no typos or misplaced characters. If the error persists, revert to the backup of your .htaccess file or use the default WordPress .htaccess template.
What are the risks of manually editing the .htaccess file?
Manually editing the .htaccess file carries risks such as site downtime, blocking yourself or search engine crawlers, and causing 500 Internal Server Errors due to syntax mistakes. Always back up the file before making any changes and follow best practices to minimize these risks.
Is there an easier alternative to configuring .htaccess manually?
Yes, using security plugins like MalCare offers a comprehensive and automated way to protect your WordPress site. MalCare handles essential security tasks such as XML-RPC disabling, file access limiting, and brute-force protection, reducing the need for manual .htaccess edits.
Category:
Share it:
You may also like

WordPress Nonce – All You Need To Know About It
Ever clicked a link on a site and gotten a confusing error message instead of the page you expected? Maybe you were trying to submit a form or delete a…
2 Simple Fixes For index.php File Corrupted on WordPress Site?
Dealing with broken links and jumbled pages is not fun, and it’s definitely not what you want your visitors to see. A corrupted index.php file is a common reason for…

How to Check if Google is Indexing My Site? – 4 Easy Methods
You just launched a shiny new site. You’ve put in hours crafting content and setting it all up. Now, you eagerly wait for it to appear in Google search results….
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.